
I think there's an issue with my storage device, but I'm not sure Start a free evaluation →
I need help getting my data back right now Call now (800) 972-3282
In the world of online business, keeping data safe helps businesses succeed in the long run. Plus, it makes customers trust them. Also, data security keeps businesses compliant with Canadian data privacy regulations. As businesses increasingly digitize their operations, the demand for robust security and data loss prevention measures also grows.
However, in recent times, the prevalence and complexity of data breaches have soared to concerning heights. This trend presents significant obstacles for online enterprises.
Cybercriminals are ceaselessly crafting innovative methods to exploit vulnerabilities, resulting in dire repercussions such as financial setbacks, tarnished reputations, and legal implications.
How data loss impacts online businesses
In the online business sphere, data loss involves the unintentional or unauthorized disappearance, corruption, or destruction of digital information. There are several causes for these, like accidental deletion, hardware failure, cyberattacks, or human error. The compromised data includes critical business information such as customer details, financial records, and proprietary data.
The potential repercussions of data loss for online businesses are diverse. Financial losses may arise from the compromised critical data. This could lead to expenses related to recovery, potential legal fines, and a direct impact on business operations. Reputation damage is another significant concern, impacting customer trust, brand image, and loyalty. The legal implications depend on the nature of the lost data and the applicable data protection regulations. This could potentially lead to legal actions and fines.
Key data loss prevention (DLP) strategies
Implementing effective data loss prevention (DLP) strategies is crucial. It helps to mitigate risks associated with various threats like cyber-attacks, human errors, and system failures.
In this context, a comprehensive approach involves strategies. These strategies create a robust defence against potential data loss incidents. It ensures the continuity and security of business operations.
Employee training
Educating employees on security best practices is a fundamental step in preventing data loss. By raising awareness about potential threats such as phishing attacks and emphasizing the importance of strong passwords, employees become active participants in fortifying the organization’s digital defences.
Encryption protocols
Implementing encryption protocols is essential for protecting sensitive data from unauthorized access.
Encryption converts information into a code, and only those with the designated key can decipher it. This ensures that even if data is intercepted, it remains secure and confidential.
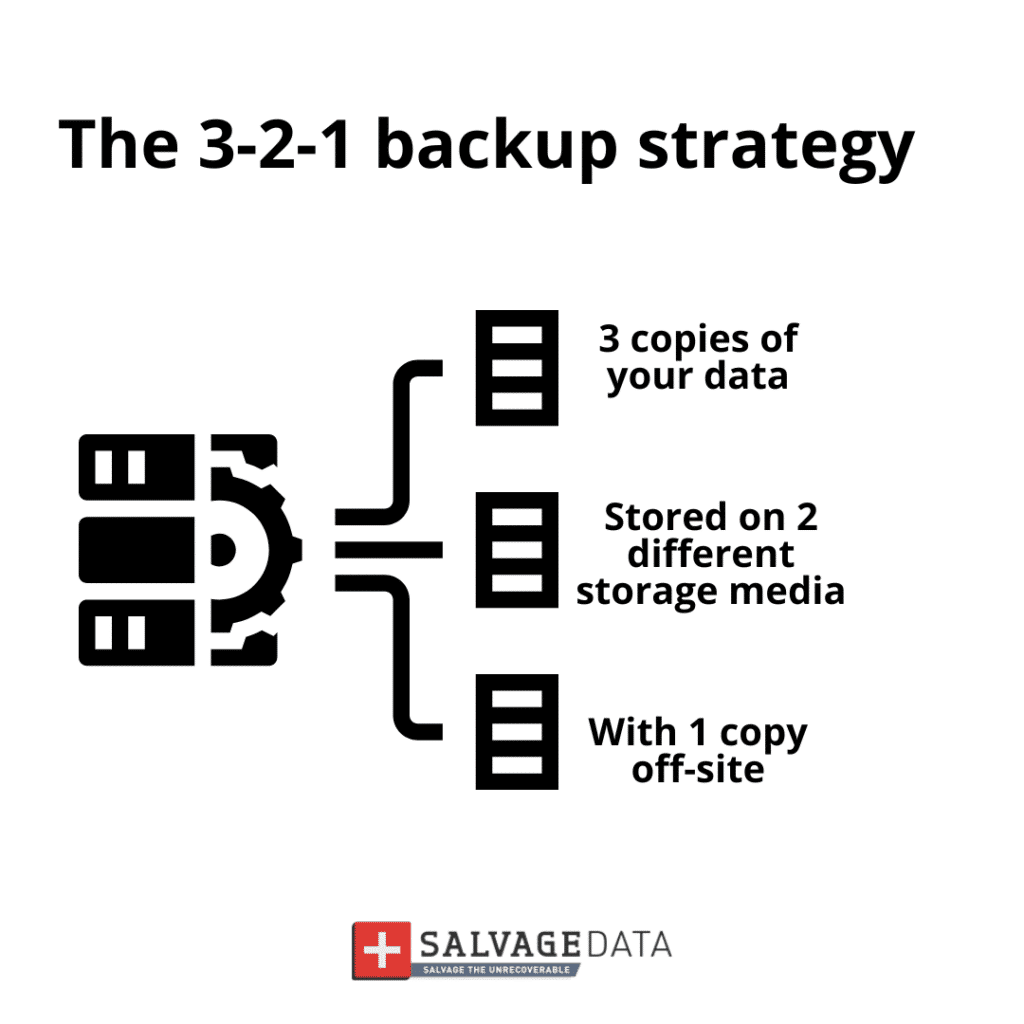
Regular data backups
Routine data backups are a cornerstone of data loss prevention. Having up-to-date backups allows for swift recovery in the event of a system failure, cyberattack, or accidental deletion. It minimizes the impact of data loss incidents on business operations.
Access control measures
Applying strict access controls defines who can access sensitive information within the organization. By assigning access levels based on job roles and responsibilities, businesses can minimize the risk of unauthorized individuals compromising critical data.
Endpoint security
Deploying security solutions on individual devices or endpoints is crucial. It helps prevent malware and unauthorized access. An endpoint is a device or node in a network, typically a computer or other device, where data is originated, processed, or transmitted.
Endpoint security tools detect and mitigate threats at the device level. They add an extra layer of defence against potential data breaches.
Assessing risks
This strategic approach enhances the organization’s resilience against potential data loss incidents. It also ensures that protective measures remain effective in an ever-changing digital landscape.
Develop security policies
Creating comprehensive security policies that outline acceptable use, data handling procedures, and security protocols provides clear guidelines for employees. Consistent adherence to these policies enhances overall data protection.
Build an incident response plan
An incident response plan is a structured and documented approach. It outlines the actions, processes, and procedures an organization follows. The plan responds to a cybersecurity incident or data breach.
An incident response plan helps organizations effectively manage and mitigate the impact of security incidents. It provides a clear framework for identifying, containing, eradicating, recovering from, and learning from such events.
A structured incident response plan is crucial. It helps respond effectively if data is lost or breached.
Common causes of data loss
Understanding the common causes behind data loss is the first line of defence for businesses and individuals alike. From hardware failures and software issues to human errors and cyber threats, various factors pose risks to the integrity of critical information.
System failures
System failures refer to unexpected malfunctions or breakdowns in a computer system’s hardware or software components. These failures can result from various factors. These include hardware defects, software bugs, power outages, or issues within the operating system.
System failures may cause data loss, disrupt operations, or completely halt the affected system.
Cyberattacks
Cyberattacks involve malicious actions or attempts to exploit vulnerabilities in computer systems, networks, or software. Cybercriminals use various tactics. These include malware, phishing, and ransomware. They aim to gain unauthorized access, steal sensitive information, or disrupt digital operations. Cyberattacks often aim for financial gain, data theft, or harm to the targeted individual or organization.
Human error
Human errors are unintentional mistakes or actions made by individuals. These mistakes lead to undesirable outcomes, such as data loss or security breaches.
Examples of human errors in the context of cybersecurity include accidental deletion of important files, falling victim to phishing scams, or misconfiguration of security settings.
Security measures are in place. However, human errors remain a significant factor in cybersecurity incidents.
Summary
In the online business world, keeping your data safe helps ensure long-term success and customer trust.
Data loss can happen due to accidents, technical problems, cyber-attacks, or human mistakes. This puts crucial info, like customer details, at risk. It can also lead to financial losses and damage your reputation. Therefore, it’s vital to have strong strategies to prevent data loss.
To protect against data loss, make sure your team knows about security and applies it daily.
If you need help with data loss prevention and recovery, turn to SalvageData Canada. Contact our data recovery experts 24/7 to protect your digital assets and recover from data loss.